Category Archives: Cyber Security
Time to reassess what is good, what is bad, and what is ugly about India’s tech regulations
The emergence of new technologies has digitalised markets, societies and nations. Once perceived as a strength, this proliferation of technology is now also a vulnerability. It has made tech-governance more political and social, and less about the traditional modes of regulation such as permissions, standards and tariffs.
India is among the most technology adept nations, a function of its people’s comfort with IT products and services as well as its late-mover advantage. It must now engage with a spectrum of evolving needs around law and regulation. This is necessary to accelerate population-scale opportunities and address widespread risks.
Three sets of issues emerge here – understanding the nature of technology-linked risks; assessing the challenges to governance; and being imaginative in embracing new modes of regulation.
Three sets of issues emerge here – understanding the nature of technology-linked risks, assessing the challenges to governance, and being imaginative in embracing new modes of regulation.
Let us begin with the risks, which themselves are creations of enhanced democratic access. For example, in roughly two decades India has added over a billion mobile phone subscribers, with over 50 per cent of them now using smartphones. This is transformational and unprecedented.
Improved access is credited with enabling financial inclusion, efficiency in education and healthcare, and fostering local e-commerce as well as global trade. However, a large user base is also a double-edged sword. As a result, corrective interventions need to be nimble and at digital velocity and population scale. Legacy regulation is simply ineffective.
This is best illustrated by problems plaguing social media platforms. A 2021 study found a high rate of social media misinformation in India, and attributed this in part to the country’s higher Internet penetration rate, driven by smart phones. Between June-July 2021 alone, Facebook received 1,504 user complaints in India – with a significant proportion of these related to bullying, harassment or sexually inappropriate content. Concerns are also emerging across other digital ecosystems, such as online gambling and crypto-assets. The mobile phone is a communication device, a crime scene and also an unsafe personal space.
Several state-level laws regulate or entirely prohibit betting and gambling. However, research suggests India is among the top five countries in terms of income potential from online gambling, and that the domestic online casino market may grow by 22 per cent each year. People from several states, such as Maharashtra, Telangana and Karnataka, are among the most frequent visitors to online gambling websites. The market for illegal betting and gambling in India is highly lucrative, with some estimating its value at USD 150 billion.
Offshore gambling websites often channel black money, engage in illicit transactions and launder wealth through financial intermediaries. Their operators are invariably based outside India, which makes it difficult to enforce the writ of the state. Recent investigations by bodies like the Enforcement Directorate have revealed instances of locals being hired to open bank accounts and trade through various online wallets, revealing gaps in due diligence mechanisms.
For the digital economy to flourish, it is important to evolve approaches that help resolve systemic and structural risks. It is time to reassess what is good, what is bad and what is ugly in this new digital landscape. Online gaming and online gambling must not be conflated. Similarly blockchain and sensible DeFi must not be clubbed with predatory crypto-gaming. After all, if we don’t embrace disruptive technology markets through sensible regulation, others will. A failure to capitalise may see India lose key avenues for economic growth and investment. India risk environment will then be shaped by external jurisdictions, some inimical to the country.
For instance, there are approximately 15 million crypto-asset investors in India, with total holdings of INR 400 billion. However, the regulatory and policy uncertainty has compelled crypto-asset entrepreneurs and exchanges to look to operate in more favourable markets. Exchanges such as Cryptokart, Koinex and ZebPay have exited the Indian market. ZebPay, for instance, is now headquartered in Singapore. In late 2021, many crypto-asset founders in India were considering moving their businesses to either the UAE or Singapore.
What we need today is new thinking and a new imagination of the digital world as not merely a virtual extension of the real, but an entirely different paradigm.
By banning cryptocurrencies altogether, nations such as China have missed the bus. India must leverage its position as the world’s third-fastest growing technology hub and seize the opportunity created by Beijing’s command and control ethos that is antithetical to innovation. India can and should become a global norms shaper in tech.
Tech regulation at population scale is akin to writing a new constitution for a digital nation. What we need today is new thinking and a new imagination of the digital world as not merely a virtual extension of the real, but an entirely different paradigm. There needs to be a clear-eyed understanding of what is legal, what is illegal and what may be illegal and yet requires regulations to serve and protect users and citizens.
To use a real-world analogy, since the 1990s, many countries including India have consistently distributed condoms and undertook safety campaigns among sex-workers without legalising prostitution or made available safe syringes to drug users without legalising the act. For governments and regulators, the role is no longer one of a gatekeeper that has the ability to prevent or permit activities online; it is becoming more of an ecosystem shaper and reducer of public bads.
By taxing cryptocurrency assets but not recognising these as legal tender, India has shown some welcome flexibility. It would do well to retain this nimbleness and become a co-curator of relatively safe tech platforms, services and products of the future that respond to Indian jurisdiction rather that off-shore the production of risks along with the rewards.
Made in China: A Digital Agenda for the Quad
In the Indo-Pacific and beyond, China’s growth in capabilities and political authoritarianism are now threatening to alter how we engage with technology and digital domains. China believes it has the right to access other nations’ information and networks without offering up access to its own. This is not a simple techno-mercantilism. There is a single purpose to China’s deepening investments in existing and future technologies: furthering the agenda of the Chinese Communist Party (CCP).
For Beijing, technology is about both national security and ideology. Under Xi Jinping, it will use the information age to rewrite every assumption of the postwar period. Countries outside China must join together to seek open, safe and inclusive technology and digital platforms and products.
There are five main ways in which we can shape national, regional and global engagement with our digital world. These must also drive the purpose and direction of the Quad countries (the United States, Australia, Japan and India) as they strive to create a technology and digital partnership in the Indo-Pacific.
‘China tech’ was for the CCP initially about managing the social contract within China. Now, the CCP is weaponising and gaming other nations’ democracies, public spheres and open systems. It is creating a digital insurgency that allows it to delegitimise its opponents on their own political turf. This goes beyond episodic interference in elections. The CCP uses American forums such as Twitter and Facebook to critique the domestic and foreign policy of nations such as India. Wolf warriors seek to shape the information space internationally while China and the CCP remain protected behind the Great Firewall. The unimpeded global access China is allowed under some perverse notion of free speech must be questioned; internet propaganda endorsed by authoritarian regimes cannot and should not go unchecked. As a first step, the world will have to embrace a political approach to repel the digital encroachments we are witnessing. The European Union offers a model – just as its General Data Protection Regulation sought to rein in the US technology giants, we need laws that limit China’s access to the public spheres of open societies, thereby curtailing its global influence.
Today, all digital (silk) roads lead to Beijing. Many developing countries rely on China for their technology sectors. From control over rare earths and key minerals to monopoly over manufacturing, China commands the digital spigot. The Quad countries and others in the Indo-Pacific must seek and encourage diversification. Affordable, accessible products and innovations must emerge in the digital space. From resilient supply chains to diversity of ownership, a whole new approach is needed to prevent the perverse influence of any single actor. This is the second way to shape global patterns of digital engagement.
The Chinese under Xi have embraced the dangerous essence of the Chinese phrase ‘borrowing a boat to go out to the sea’. The CPC has essentially borrowed all our boats to further their agenda.
Universities in the developed world, their media, their public institutions and even their technology companies are serving and responding to missives from the Middle Kingdom. Many journalists have exposed the Western media’s promiscuous entanglements with a Beijing that artfully co-opts them into its propaganda effort. In the digital age, this cannot be ignored. Countries will soon be faced with a digital fait accompli – signing on to Pax Sinica. As a third way to enhance engagement, it is time to protect liberal institutions from their own excesses.
China has attempted to internationalise its currency with the launch of its own digital currency. After banning financial institutions and payment companies from providing crypto-related services in May, China launched a crackdown on computer-powered crypto mining in June, and a blanket ban on all crypto transactions and mining in September, clearing the way for its digital renminbi (digital RMB). With the development of its own central bank digital currency, the Chinese government will now have the power to track spending in real time. It will have access to the entire digital footprint of a citizen or a company. This will provide Beijing with an unprecedented vault of data, which it can use to exercise control over technology companies and individuals.
The rise of China’s digital RMB has the potential to challenge the status of the American greenback. For decades, the US dollar has been the world’s dominant reserve currency. Yet countries such as Iran, Russia and Venezuela have already begun using the Chinese yuan for trade-related activities or replacing the dollar with the yuan as reference currency. China can shape all three attributes of the ‘ideal’ currency, also referred to as the ‘Impossible Trinity’: free capital flow, a fixed exchange rate and independent monetary policy. It is a matter of time before it uses currency as part of its wider geopolitical plans. And with its past experiments with many countries on ‘trade in local currency’, it will have the capacity to create disruptions in the global monetary system. This can only be countered with two measures: one, depoliticising the existing dollar-led currency arrangements (the tendency to weaponise the SWIFT system – a giant messaging network used by banks and other financial institutions to transmit secure information – and to employ ad-hoc economic sanctions) and two, investing in the economic future of the emerging economies that currently depend on China.
Lastly, China is seeking technological domination not only terrestrially but also in outer space. China has invested considerably in space technology and engages in counterspace activities. These include suspected interference in satellite operations, both through cyberattacks and ground-based lasers. There are growing fears that Chinese technologies developed for ostensibly peaceful uses, such as remote satellite repair and cleaning up debris, could be employed for nefarious ends. The inadequate space governance mechanisms is an opportunity for the Quad to develop situational awareness in the space realm to track and counter such activities, and to develop a new set of norms for space governance.
The Quad’s agenda is prescribed by China’s actions. It will have to be a political actor and have the capacity to challenge China in the information sphere and the technology domain. It will need to be a normative power and develop ideas and ideals that are attractive to all.
From codes and norms for financial technologies to the code of conduct for nations and corporations in cyberspace and outer space, the Quad has the responsibility and opportunity to write the rules for our common digital future.
The Quad will also have to be an economic actor and build strategic capacities and assets in the region and beyond. It will have to secure minerals, diversify supply chains and create alternatives that ensure the digital lifelines are not disrupted.
Most importantly, the Quad will need to be an attractive partner for others to work with. This is its best means to counter China’s dangerous influence.
Amid changing post-pandemic realities, India needs to be swift in identifying partners whom it can trust
We will see the rise of a New World Order driven by national interest, reliability of partners, and of course, economic factors. India has to use a “Gated Globalisation” framework to negotiate this change.

The COVID-19 vaccines are coming. And along with this sanjivani comes a new age of geopolitics. The vaccines are varied, with different pricing points and affordability. Nations have secured their vaccine supplies from countries and companies they trust, often by forging new alliances. The scepticism over the vaccines from China and Russia shows that trust is the operating word in the post-pandemic era — and it is not limited to the choice of vaccines.
As we enter the third decade of the 21st century, a multipolar world awaits us. The US and China — rivals for the top slot till the pandemic hit the world — will now have to contend with traditional and rising powers like the UK, France, India and Brazil. Each country will engage with others selectively, not in every arena. We will see the rise of a New World Order driven by national interest, reliability of partners, and of course, economic factors. India has to use a “Gated Globalisation” framework to negotiate this change.
The security landscape will continue to drive partnerships, but these will no longer be omnibus alliances. India is locked in a confrontation with China in the Himalayas. The US and its traditional allies are ramping up their presence in the Western Pacific. A new Great Game is underway in the Indo-Pacific where the Quad is emerging. The Middle East is in a deep churn as Israel and Arabs discover Abrahamic commonalities. Europe is caught in a struggle to retain its values amid the diversity it has acquired over the years.
The Gated Globalisation framework requires that India should protect its interests in these unsettled times. Strong fences are necessary, but so is the creation of new partnerships (like the Quad) based on trust and common interests. Gated Globalisation has no place for parlour games like “non-alignment”; it will test the tensile strength of “strategic autonomy”. The need for a new coalition was felt after Doklam and has become a necessity post-Ladakh: India needs friends in deed.
The Gated Globalisation framework requires that India should protect its interests in these unsettled times. Strong fences are necessary, but so is the creation of new partnerships (like the Quad) based on trust and common interests
Beyond security, like everybody else, India has to make partnership choices on trade, capital flows and the movement of labour. The WTO’s multilateral trading arrangements have frayed beyond repair. Whether it is RCEP in the Indo-Pacific, the new version of NAFTA called USMCA, or the reconfigured EU, countries will have to decide whether they belong inside these gated trading arrangements. India has chosen to stay out of RCEP and the UK has left the EU.
By imposing restrictions on trade with China, India faces restrictions on capital flows. But this does not preclude enhanced capital flows from new partners. To prevent inflow of illicit funds, India has barred capital from poorly-regulated jurisdictions. India’s capital account for investment is largely open while its current account is carefully managed. Similarly, while restricting debt flows, India is open for equity flows from friendly countries. Other nations have similar policies. By managing capital flows in this manner, countries have enabled tighter financial relationships within their gated communities while shutting out those who are inimical to their interests.
India’s global diaspora is now over 30 million and sends more through remittances ($80 billion per year) than foreign capital inflows. The pandemic-enforced work-from-home may see the creation of new pools of skilled workers, living in virtual gated communities, further enhancing income from jobs physically located elsewhere. Moreover, the Indian diaspora is now increasingly impacting policy in countries like the US, UK and Australia where it has contributed politicians and technocrats, innovators and influencers, billionaires and cricket captains.
The pandemic-enforced work-from-home may see the creation of new pools of skilled workers, living in virtual gated communities, further enhancing income from jobs physically located elsewhere
Finally, technology flows and standards will also define gated communities. The internet is already split between China and everyone else. The Great Firewall of China has shut out many of the big tech players like Google, Facebook and Netflix. Instead, China has its Baidu, Alibaba and Tencent. With the advent of 5G technology, this split will get deeper and wider over issues of trust and integrity.
The EU-crafted General Data Protection Regulation (GDPR) is an excellent example of Gated Globalisation. The EU has set the terms of engagement; those who do not comply will be kept out. The Indian law on data protection that is currently being discussed follows a similar sovereign route. However, it remains to be seen whether these norms can checkmate China’s massive digital surveillance apparatus.
There are other emerging arenas that will likely become the focus of big power competition. China has moved in all possible directions to develop its global strategies. It has linked its national security interests with its Belt-and-Road Initiative and its debt programmes. It is offering a package deal of 5G technology with new telecom networks. China has learnt well from the US.
Amid these rapidly changing post-pandemic realities, India has to be swift in identifying partners whom it can trust and who will help protect and further its national interests. Ambiguity, lethargy and posturing will not do.
On the Cusp of Digital History: Nine Lessons for the Future
s we step into a year of uncertainties after a disruptive year of the pandemic, there is only one universal certitude: 2021 will witness the increasing adoption of technology as innovation gathers extraordinary speed. Clearly, our digital future is exciting, but it is hazy too. There are galactic black holes; and even that which is visible is overwhelming.
Despite acknowledging the need for critical discourse, our pace of enquiry, examination and action has been lethargic and out of step with the motivations of coders hardwiring our future through soft interventions. They are changing economies, societies, politics and, indeed, the very nature of humanity at an astonishing speed and with far-reaching consequences.
Nations that effectively respond to the advent of the Digital Era will be in the vanguard of the Fourth Industrial Revolution and will emerge stronger as the 21st century approaches high noon. Others will suffer the adverse consequences of the coming digital disruptions.
At the turn of the decade, Delhi hosted a stellar set of thinkers and speakers at the annual CyFy conference organised by the Observer Research Foundation, which focused on technology, security and society. Here are nine takeaways from the debates and discussions that threw up a kaleidoscope of scintillating ideas.
1. CHINA’S DIGITAL VICTORY PARADE
hat the US accomplished in the 20th century, China has set out to achieve in the 21st. The first takeaway from the CyFy debates is that China’s surge will continue, and it will profoundly change the world order. The US and its partners are witnessing the inexorable rise of an authoritarian digital power with the COVID-19 pandemic emboldening
THE US AND ITS PARTNERS ARE WITNESSING THE INEXORABLE RISE OF AN AUTHORITARIAN DIGITAL POWER… CHINA’S SURGE WILL CONTINUE, AND IT WILL PROFOUNDLY CHANGE THE WORLD ORDER.
Beijing to tighten its surveillance and suppression networks—bolstered by big data, facial recognition, et al.
The China Electronics Technology Group Corporation (CETC), a defence contractor, for instance, pitches such future applications as detecting ‘abnormal behaviour’ on surveillance cameras or among online streamers. These applications intimate such detections to law enforcement agencies.[i] Several regimes around the world are attracted to these Chinese offerings, which enable them to control their citizens.
Meanwhile, the old Atlantic Consensus is in total disarray. Europe is intent upon carving out its niche in emerging technologies while promoting new technology champions to challenge American tech dominance. After taking over the European Union presidency, Germany has called for the expansion of digital sovereignty as the leitmotif of EU’s digital policy.[ii] A new Digital Services Act may fundamentally alter intermediary liability and mark a new milestone in digital rights and freedoms.[iii]
Across the Atlantic, the US has made its fear of China Tech apparent but is yet to initiate a coherent effort to build an influential digital alliance as a sustained response to China’s relentless digital expansionism. Which brings us to the central geopolitical question: Can the US and Atlantic nations, currently marred by divisions and domestic disquiet, get their act together to respond to this emergence? Authoritarian tech is at the gates: Does the West have the resolve to respond? Will a new Administration in Washington, DC herald a new and meaningful approach? Or will America continue to turn inwards?
China will not offer any negotiated space. Beijing’s offer will be binary, so will be the outcomes. It is, therefore, imperative for a club of technology-savvy countries to come together if liberalism is to be preserved in our digital century.
2. END OF MULTILATERALISM AND THE RISE OF CLUBS OF STATES

o say that the international order is failing and floundering is not to state anything startlingly new; it’s only to underscore the bleakness of the global reality. However, like the proverbial silver lining, there is a degree of optimism around the role and centrality of smaller groupings. Regional partnerships, alliances of democracies, and plurilateral arrangements between nations with focused engagements and specific purpose platforms are seen to be important in these turbulent times. This is best exemplified by Australia, India and Japan—who with an eye towards China and propelled by their shared interest in a free, fair, inclusive, non-discriminatory and transparent trade regime—are banding together for a Supply Chain Resilience Initiative.[iv]
These small groupings, built around shared but limited objectives, are dying multilateralism’s lifeline. The Year of the Pandemic and its resultant disruptions have left the world with few options. One of them is to begin rebuilding multilateralism with smaller groups of countries with aligned interests. Hopefully, over time, this will lead to an efficient, inclusive international order.
India, Japan and Australia have taken on the responsibility abdicated by the US of building a resilient, vibrant, secure technology network in the Indo-Pacific. The role of the EU, ASEAN (more difficult due to deep divisions) and democracies in the Indo-Pacific in defending and strengthening norms and laws associated with technology and politics was elaborated loudly and clearly at CyFy.
States matter and the leadership of individual nations will have to drive the global arrangements that will best serve this century. While dialogue with geopolitical adversaries remains critical, meaningless consensus-driven multilateral approaches are not viable in a world fundamentally fractured along political, economic and ideological fault lines. We need action, not pious declarations. Given the pace at which emerging technologies are evolving, organisations like the UN are too slow, unwieldy and politically compromised to have any significant impact.
3. GLITCH IN GLOBALISATION

n the post-COVID-19 era, globalisation as we have known it will be in tatters, yet decoupling will be more difficult than before. There is a simplistic assumption that you can decouple your digital world from the real world. This is not so. If you exclude entities from your digital platforms, it will be difficult to sustain traditional trade in goods and services with them. Commerce and connectivity of the future will have a different texture.
As economic growth, national identities and digital technologies collide, “Gated Globalisation” will be the new mantra. With interdependence no longer fashionable, supply chains will be shaped by rising national security concerns. Increasingly, cross-border flows of data, human capital and emerging technologies are viewed as vulnerabilities. A focus on autonomy and indigenous capabilities has accompanied growing incidents of cross-border cyber operations and cyberattacks.
Commerce may be conditioned on norms along the lines of what the General Data Protection Regulation (GDPR) seeks to do with the digital economy. The Blue Dot Network and supply chain initiatives may all end up creating layers of permissions and permits that will create toll plazas on digital freeways. The digital domain was built on the assumption of hyper interconnectedness. Will it be able to grow with mushrooming policy barriers?
4. UNCHARTED TERRITORY: BETWEEN TECHNOLOGY AND STATE
new and fascinating dynamic is rapidly emerging between democracies and technologies, raising an interesting question: If a democratic state tames technologies, can democracy survive? This question has been posed by Marietje Schaake, the International Policy Director at the Stanford Cyber Policy Center.[v] Technology is being co-opted into a ‘techno-nationalist’ narrative: The melding of a country’s national interest with its technological capabilities while excluding ‘others’. This techno-nationalist narrative often emanates from tech giants who are increasingly speaking in the state’s protectionist language. Mark Zuckerberg’s written statement ahead of US Congressional anti-trust hearings was couched in the language of protecting the core American values of openness and fairness, as opposed
IF A DEMOCRATIC STATE TAMES TECHNOLOGIES, CAN DEMOCRACY SURVIVE? THE COROLLARY TO THAT IS EQUALLY TRUE AND PROMPTS ANOTHER QUESTION: CAN DEMOCRACIES SURVIVE IF THEY DO NOT REGULATE TECHNOLOGIES?
to China’s (authoritarian) vision.[vi]
The corollary to that is equally true and prompts another question: Can democracies survive if they do not regulate technologies? The isolating and polarising effects of social media, for instance, have already resulted in a slew of analysts chanting the dirge for democracy.[vii] The answers to these questions are unclear, but it is certainly true that the protection of the public sphere, the integrity of political regimes, and the robustness of conversations must be common aspirations should we want democracy to survive and strengthen.
Be it regulations, education, incentives, ethics or norms, we will have to dig deeper into our toolbox to come up with answers that would allow this to happen. Currently, the negative impacts of technology on our evolving and fractured societies are threatening to overwhelm its promise and potential. Can a new regulatory compact emerge that negotiates the digital ethics for corporations, communities and governments? This decade will witness an unspoken contest over writing this new code of ethics. It remains to be seen whose code will prevail and, more importantly, for what purpose.
5. UNACCOUNTABLE TECH AND CORPORATE BOARDROOMS
e cannot overlook the changes that the relationship between big companies, technology and societies has undergone. If successive anti-trust actions in the US, EU, Australia, India and elsewhere are any indication,[viii] accountable boardrooms are now an expectation and will soon be a reality; the shape it will take will be defined by the debates taking place around the world. We can be certain that in the coming years, corporate governance is not going to be the same.
Large companies, having dominance and influence, will need to be more responsive to the communities they serve. The blueprint of new corporate governance cannot but be influenced by the needs of the locality; the nature of the framework will have to be contextual and culturally sensitive. Since mammoth corporations determine our very agency and choice, it is part of their fiduciary duty to ensure that the interests of the company and the community are ethically aligned.
Outside corporate boardrooms, we cannot ignore the role of coders or programmers in Bengaluru, Silicon Valley, Tel Aviv and other tech hubs. As we become increasingly reliant on software, can we let coders be the new cowboys of the Wild West without any accountability? As we get further entangled in the intricate web of algorithms, it has become clear that we need to demystify them. No more black box responses, no more unaccountable algorithms. What we need are programmers who are held responsible for the impact their codes make on people’s lives. We need algorithms that are not only transparent but also seen to be so.
6. THE PANDEMIC & DIGITAL SOCIETIES

he pandemic has made us reassess our approach to life and behaviour. We consume, we communicate, and we integrate using technology. Nearly a year on, COVID-19 has not only furthered technology’s invasion of our lives but also brought to the fore new realities, especially regarding privacy. The deepening concern over privacy is intertwined with the change in the ownership of data. The pandemic provided the pretext to alter the role played by big corporations and the control of the state over technological devices, products and services.[ix]
The digitalisation of our day-to-day lives may enable an unprecedented level of personalised oversight over individual behaviour. In its mildest form, this can be ‘libertarian paternalism’, a nudging predicated on the belief that individual choices are rarely made on the basis of complete information and are instead a product of psychological biases. At the other end of the spectrum, the ‘gamification’ of citizenship under this new paradigm would be the ultimate realisation of the Hobbesian social contract, whereby the Leviathan would be entrenched in every aspect of citizens’ lives.
In order to retain the ownership of data and individual autonomy, all these changes must be accompanied by the strengthening of our resolve to defend individual choice, freedom and rights by formulating adequate laws that would ensure that the values we create serve us, the people.
7. REWRITING THE SOCIAL CONTRACT

he world needs a new social contract—a digital social contract. The pandemic has thrown the old workplace order into a state of flux, thereby, reopening the debate surrounding the provision of the three Ps: Paycheck, protection and purpose to individuals. The equivalent of 475 million full-time jobs vanished in the second quarter of 2020[x] and many others found themselves without health insurance and other benefits typically linked to work contracts at the greatest time of their need. To ‘build back better’, the new order is being shaped by new terms of contract and employment, concepts of social protection and minimum wage for all, and the altered role of the state, big tech and individuals. The global shift towards virtual workspaces also provides an opportunity to induct a more diverse work force, especially individuals from historically marginalised communities. However, we need to take note of the challenges that might accompany these changes—such as ensuring safe, inclusive digital workspaces, keeping pace with ever-changing technology, meeting the demand for human skills, and coping with the displacement of jobs. As we move to a more ‘virtual first’ work environment, we need to make sure that nobody is left behind.
Meaningful engagement with vulnerable communities necessarily involves outreach by governments as well as large technology firms, both of whom have benefited from the data of these communities. It is, therefore, the responsibility of both to build bridges with the communities that would be most vulnerable to the disruptive impact of the technologies they build and benefit from. We must take advantage of this moment to forge technology that will be in service of humanity—taking ‘people-centered innovation’ from a buzzword to actual practice.
8. OUTLASTING THE VIRUS: INFODEMIC AND I
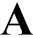
n intense battle is being waged against the Infodemic, which is running parallel to the battle against the Pandemic. Misinformation, the darkest shade of grey in the Chrome Age, is now being used to destabilise businesses and political systems, and dissolve the social cohesion shared by individuals. “Misinformation costs lives”,[xi] and the Infodemic has led to uncountable preventable deaths.
NO SINGLE AGENT CAN EVER ENSURE THE INTEGRITY OF THE GLOBAL INFORMATION SYSTEM. THE ANSWER, THEREFORE, LIES IN THE COMING TOGETHER OF ALL THE THREE IMPORTANT ACTORS—THE STATE, BIG TECH AND THE PUBLIC.
No amount of digital distancing is helping curb the spread of fake news. This emergence of a highly polarised information system should be effectively countered by a new guarantor of the public domain. No single agent can ever ensure the integrity of the global information system. The answer, therefore, lies in the coming together of all the three important actors—the state, big tech and the public.
The state should help denounce disinformation and simultaneously promote high quality content. Big tech can devise algorithms to filter out such misinformation, curtail the financial incentive acquired through it and display a higher sense of responsibility. Indeed, if platforms can display the same energy and responsiveness they did during the US elections in other jurisdictions, we may have some hope for a tenable solution.
Finally, the public should expand their information base by incorporating different sources of information, reading before posting on social media, and exposing and reporting fake news. It is only through the realisation of collective responsibility that we can hope to find a ‘vaccine’ for the Infodemic.
9. #TECHFORGOOD – A RAY OF HOPE

n a gloomy landscape of various shades of grey, we are at last beginning to see some light and some white. The emergence of a technology moment where communities are beginning to find their voices and change the course of their future, provides a glimmer of hope. Across the world, especially in Asia and Africa, people are discovering, nurturing and shaping new aspirations and goals for themselves by using technology. The African Union highlighted the need to diversify, develop and assert ownership over its digital society and economy.[xii] Community data has transformed from a fringe idea to a mainstream policy debate, receiving a nod, for instance, in India’s Non-Personal Data Governance Framework.[xiii]
Even as the pandemic upended our lives, we saw governments deploying technology for the greater social good; we saw businesses respond to it with extreme ingenuity; and we also saw women seizing this moment and retaining agency.
The post-pandemic era offers us an opportunity to build a more diverse and inclusive digital order. We can, and must, redefine diversity and support minorities and women to play a key role as a new world emerges from the debris of the war on COVID-19. The world today once again stands on the cusp of history. It cannot afford to fail in laying a new foundation which is free of the of the frailties of the past.
Technology and Terror: A new era of threat in a borderless online world
Terror requires spectacle to thrive and technology has allowed this opera of violence to find new audiences and locales.

From ISIS attaching a GoPro camera to a home-made armed drone in Syria to Islamists from the Democratic Republic of Congo uploading 4K videos pledging allegiance to Abu Bakr al-Baghdadi, cyberspace and emerging technologies are facilitating terrorist activities at an unprecedented scale. The convergence of technology and terrorism represents the worst kind of feedback loop between the real and the virtual. States, meanwhile, are struggling to respond to this convergence and to balance the imperatives of national security and the freedoms afforded in cyberspace.
Given the complex structural drivers of terrorism and the trade-offs involved in regulating technology, it is imperative that policy makers first assess the real and evolving dimensions of the challenge. The popular conceptual understanding of this menace is that like war, terrorism is simply politics by other means. Whoever the actor may be, terrorism is a violent expression of alternative political values and norms for organizing societies. Motivations may vary but violence is the principal instrumentality for recruiting, propagating and financing this perverse politics. And like mainstream politics, terrorist organizations have co-opted technology as a force multiplier in achieving their objectives.
Like mainstream politics, terrorist organizations have co-opted technology as a force multiplier in achieving their objectives.
As has been suggested by many scholars, terror requires spectacle to thrive and technology has allowed this opera of violence to find new audiences and locales. The Christchurch shootings in New Zealand is perhaps the most obvious example — with the shooter streaming his actions live on social media. New communication platforms afford scale and impact at virtually no cost, a service that terrorists have used with impunity and agility over the years with deleterious consequences for communities and countries.
Some features of the internet, like end-to-end encryption and virtual private network (VPN) have made it easier than ever for terrorist organizations to find recruits and manage outreach and organization. For example, migration of pro-ISIS propaganda from likes of Facebook and Twitter to Telegram was in a large part due to encryption facility offered to all its users. Technology also allows these organizations to transcend the tyranny of geography. An organization in one country can raise funds, recruit and radicalize individuals in another part of the world with ease.
Some features of the internet, like end-to-end encryption and virtual private network (VPN) have made it easier than ever for terrorist organizations to find recruits and manage outreach and organization.
Every communication opportunity online is being exploited by these malevolent actors. From the mainstream platforms such as Facebook and Telegram to chat rooms, betting sites, porn websites and online gaming hubs. These virtual venues are fertile breeding grounds for accidental and purposeful recruits and for propagating violent narratives. The importance of ‘digital terror squads’ was emphatically asserted when, in 2016, ISIS granted its ‘media mujahids’ the same rank as those fighting for the group on the ground. This gave the online radicals pride of place that was traditionally reserved for the fighters delivering carnage on the ground. This is only one of the instances that signify just how integral, sophisticated and important cyber operations are for terrorist organizations today.
Terrorist organizations are also leapfrogging traditional hawala networks to embrace Fin-Tech as a means to finance their operations. Services like e-wallets, digital currencies, crypto-currencies and even crowd funding platforms are being leveraged to raise and launder money and finance terrorist operations. This has rendered most current practices of clamping down on terror-finance obsolete, and today more terror organizations have access to more money than ever before.
Terrorist organizations are also leapfrogging traditional hawala networks to embrace Fin-Tech as a means to finance their operations.
Amidst this worrying convergence of terrorism and technology, states have struggled to respond without threatening the infrastructure of cyberspace or the freedoms and opportunities it affords. Meanwhile, the tech platforms are having troubles of their own. The word ‘social’ in social media is under scanner, with platforms facing multiple headwinds relating to their policies on responding to terrorism, fake news and political interference among others. These platforms host billions of users even as they struggle to differentiate between their ‘social’ obligations to the digital commons and their commitments to markets and investors.
As states, platforms and grassroots organizations combat the threat of tech-enabled terrorism, it is important for them to identify certain guiding principles.
First, it is crucial that they do not unintentionally limit access to technology itself. For many states, the knee-jerk response to some of these challenges is banning access or shutting down tech-based routine operations altogether—as we recently saw in Sri Lanka. Instead, states must co-opt technology and tech-actors, which allows for better surveillance of and enforcement against terrorist activities. Legislations and notifications will have limited influence in this new battle theatre. More technology, better technology and skillful deployment of technology against malign actors is the most potent option for all to embrace and one which most governments have failed to invest in.
States must co-opt technology and tech-actors, which allows for better surveillance of and enforcement against terrorist activities.
Second, the digital commons must witness the creation of new mechanisms and institutions for international cooperation on this vital issue. The challenges of terrorism are cross border — making debates held hostage by ‘regional’ or ‘international’, ‘Western’ or ‘Eastern’ silos irrelevant. States and tech companies need to find new venues and forums to cooperate on these issues in an institutionalized manner, formally or informally. The traditional distrust between governments and private actors is creating a cleavage that allows terror to flourish and succeed.
The digital commons must witness the creation of new mechanisms and institutions for international cooperation on this vital issue.
Third, technology companies must be more forthcoming about disclosures relating to terrorist activities on their platforms. The obsession with the performance of their shares on the bourses is perversely impacting the global effort to respond to terror. They must create internal mechanisms to share information with law enforcement on a real time basis. They must also publish regular public reports detailing the nature of terrorist activities they have identified, and steps taken to counter them. The reluctance of corporations to be transparent about the mishaps on their platforms and networks is a serious problem.
Technology companies must be more forthcoming about disclosures relating to terrorist activities on their platforms.
Fourth, states, for their part, must remember that tech is only a tool. It is not a substitute for real world and virtual policing. Often states attempt to undermine tech—for example through weaker encryption norms due to their naïve assessment that this would assist in their dispensation of duty. This only undermines utility and safety of technology for millions of benign users; while terrorist organizations will simply migrate to alternative platforms as witnessed in the recent past.
States…must remember that tech is only a tool. It is not a substitute for real world and virtual policing.
Fifth, localized capacity building both by state and tech firms is the need of the hour. While national intelligence organizations are certainly relevant, the first line of defense against tech-enabled terrorism will be local law enforcement. Unless these units are equipped with skills and technology, the terrorist will always remain a step ahead in an upcoming era of Do-It-Yourself (DIY) terrorism.
Localized capacity building both by state and tech firms is the need of the hour.
Finally, simultaneous investments in capacity for strategic communications by states and technology companies is a pivotal step. Unless good actors can combat the narrative appeal of radicalism and terror, most responses with be feeble and patchy. Either the states provide purpose and meaning to individuals, or radical groups will. The old methods of counter-terror will need to be dramatically upgraded and redesigned. The terrorists have developed a lethal cocktail of clicks and Kalashnikovs, even as citizens, states and other organizations, lag behind in recognizing and responding to this heady mix.
Simultaneous investments in capacity for strategic communications by states and technology companies is a pivotal step.
Any good policy response to tech-enabled terrorism must acknowledge that combating it requires an “all of society” approach. This first line of defense is always communities, no matter how the technology may change. Platforms for their part must work with them alongside states to increase awareness about this real and present danger and must transparently share their propositions that can help to balance the trifecta of growth, rights and security.